The Varnish Cache Firewall is a Web Application Firewall that can protect WordPress. It is an open source project by comotion to integrate the modsecurity web application firewall into Varnish and will help protect WordpPress against SQL injections, XSS attacks and other web attacks. This Varnish firewall tutorial is specifically for Debian but is easily adaptable to Ubuntu, CentOS, Fedora and other Linux systems. Ubuntu.
The Varnish Cache Firewall is a Web Application Firewall that can protect WordPress. It is an open source project by comotion to integrate the modsecurity web application firewall into Varnish and will help protect WordpPress against SQL injections, XSS attacks and other web attacks. This Varnish firewall tutorial is specifically for Debian but is easily adaptable to Ubuntu, CentOS, Fedora and other Linux systems. Ubuntu.
The Varnish firewall works with Varnish 4.1 only, if you are still on Varnish 3 you can use this guide. This how to assumes you already have Varnish 4.1 configured with WordPress for which there is a tutorial here for nginx and Apache. You need to have shell terminal access to your server or VPS in order to compile the required Varnish 4.1 vmods which add the firewall functionality using clever vcl files.
For Varnish 4.1 and later
Attention: this should be tested thoroughly on a development environment
| VPS Provider | |||||
|---|---|---|---|---|---|
| Vultr | |||||
| Digital Ocean | |||||
| HostUS |
Install WordPress Varnish Cache 4.x Firewall
Install Varnish vmod building dependencies
sudo apt-get update
sudo apt-get install libvarnishapi-dev libvarnishapi1 dpkg-dev pkg-config build-essential git autotools-dev automake libtool python-docutils -yBuild Varnish 4.1 and later VSF vmod which autobuilds the other required vmods.
cd ~
git clone https://github.com/comotion/VSF
cd VSF/libvmod-vsf
sh autogen.sh
./configure
cd ..
sudo make
make installThe Varnish Security Firewall has placed the required vcl files into /usr/lib/varnish/vmods and the vcl rules are in /etc/varnish/security/rules in case you need to change anything like undoing false positives.
Open your Varnish vcl to add the VSF code.
sudo nano /etc/varnish/default.vclIn your Varnish default.vcl you can add this before sub vcl_recv begins or after it ends.
Add the red line so it matches below. Alternatively, you can add the red line after your sub vcl_recv section if you are getting a lot of false positives.
} # sub vcl_recv ends
include "/etc/varnish/security/vsf.vcl";Test your Varnish firewall configuration will load
varnishd -C -f /etc/varnish/default.vclMonitor your Varnish 4.1 log for anything that is caught by the firewall and to check for false positives. You can disable the rules that are triggering false positives in the vcl files in the /etc/varnish/security/rules folder.
varnishlog -c -q VCL_LogYou can test a basic WordPress SQL injection attack like this and see that the Varnish Security Firewall prevents it
HTPC' OR 1=1 OR 'GuidesHere is a simple XSS WordPress attack, replace my homepage URL with your own.
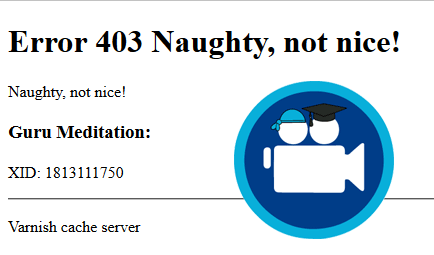
https://www.htpcguides.com/<script>alert('HTPC Guides Varnish Firewall Example')</script>You should find that both attacks result in this error message demonstrating the Varnish firewall is working to protect WordPress.
This concludes the Varnish cache firewall tutorial for WordPress and now you should be a safer from attacks.